Stop hitting snooze on security: why assessments are a wake-up call
With the release of the Autumn budget in the UK, there is an additional financial strain to cut costs, so what does that mean for your cyber security budgets? Organisations will be looking for increased evidence that their investments are justified, and cyber security is no exception.
Typically, security budgets only increase after a cyber incident occurs, which is too little, too late. So, how can your organisation budget effectively, whilst considering threats before the inevitable breach? It all starts with understanding your risk!
Understanding your risk & control investment
The Cyber Security Breach Survey 2024 states that only 31% of businesses and 26% of charities have undertaken cyber security risk assessments in the past year.
Risk is the probability of an event occurring and it’s consequence. The potential cost of risk is usually quantified in monetary value, however, it can also damage reputation which can be just as devastating. So our risks need to be understood, so they can be managed and a control is the means of managing risk.
At a recent workshop on detection & response, we conducted an exercise that explored control investment. Grouped participants had the same scenario with a theoretical organisation. They were also given a board with controls and their respective costs. If they were to buy everything it would cost £995,000, however, they were given limited budgets (£550,000).

Interestingly, each group had different results despite having the exact same scenario. They purchased security controls based on what they perceived the best investment would be given their subjective experiences. So what does this tell us? Well, firstly if you’re given a budget, you’re going to spend it! Additionally, without an objective security assessment, investment is susceptible to being subjective and non-optimal.
Effective security control investment means aligning the right control to the right risk and these risks need to be mapped to business objectives. Therefore, before rushing into a potentially redundant investment, ask yourself, what are we solving? What’s the risk we are mitigating? And, does this control support our business objectives?
After all, optimal control investment should not exceed the potential cost of losses. This is where security assessments can help. An assessment aligned with industry best practices, such as the NCSC’s Cyber Assessment Framework, can help you understand your current security posture and make informed, cost-effective decisions about the controls you invest in.
Whilst frameworks provide a foundation, they alone cannot provide assurance without the right expertise. Our solution: An experienced security partner bringing independent oversight with a proven track record across different industries & verticals.
The value of an assessment
The purpose of an assessment is to review your current security posture by examining your security objectives and detailing the controls you have in place. These controls can be administrative, like processes and policies, or technical, like firewalls and detection systems.
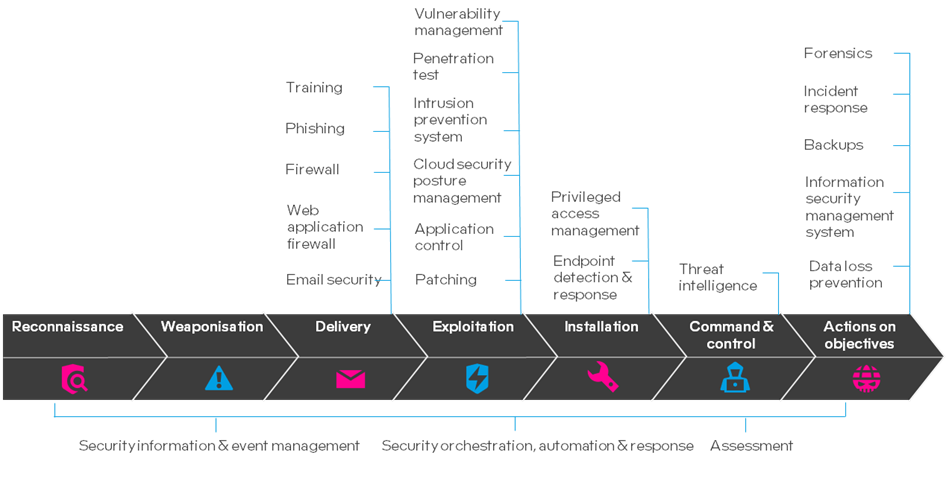
One crucial aspect of security assessments is gap analysis. We use these exercises to compare our current state to our desired state which will be aligned to industry standards & frameworks. In the example below, we have mapped the security controls from our previous exercise to the Lockheed Martin cyber kill-chain framework.
In the example we are reviewing controls from an adversarial or ‘threat’ perspective to better understand the residual risk, we can also see where controls overlap, which often can be a good thing for defence in-depth as you’re not prone to a single point of failure.
The information from exercises like these feeds into our security assessments. An assessment identifies areas for improvement, provides insight into your risk & controls, and furthermore enables your organisation to optimise control investment.
We can use these outcomes to take a proactive approach to improve our security posture and justify budget requirements to meet your security goals, so you can avoid the common pitfall of increasing funding after a data breach.
Where to start?
Longwall offers 3 different types of assessment.
Instant assessment:
The instant assessment leverages both Longwall’s cyber security expertise and the Cyber Assessment Framework (CAF) to deliver score-based outcomes and recommendations, that can go on to be tailored to each organisation’s specific needs and challenges.
Pro assessment:
Longwall’s pro assessment is designed to map to the NCSC’s Cyber Assessment Framework (CAF), offering in-depth analysis. This bespoke assessment goes beyond surface-level evaluations to highlight every component of your cyber security defences as laid out by CAF’s comprehensive criteria.
We delve into the intricate details of your security practices, exploring areas such as governance, asset management, technical defence mechanisms, incident management, and resilience planning. The pro assessment is not just an evaluation – it will serve as a strategic compass, allowing you to strengthen your security framework, ensuring it is robust, comprehensive, and forward-thinking.
Premium assessment:
Our premium assessment offers instant peace of mind. We become your security partner for the next 90 days, delivering our Managed Detection, Intelligence & Response service – alongside 2 tangible threat update meetings and our Pro assessment report.
Our two threat updates showcase our threat hunt findings, finding the real risks in your organisation such as:
- Insecure password storage
- Usage of shared administrator accounts
- Suspicious ingress authentications
- Unauthorised remote management tooling
- Information leakage on the dark web
- Riskiest devices with vulnerabilities
- Shadow IT software
- CIS Level 1 compliance
- Active default credentials
Wrapped up with a detailed report containing executive summaries, CAF-based security assessment, real-world recommendations, security objectives & strategy. All whilst being protected by our unlimited incident response, through our 24x7x365 MDIR service.
Find out more about our security assessment services.
Take our instant assessment to find out the current state of your security posture.



